Building on the features that were included in FileMaker 13 and 14, FileMaker Inc. continues to make a push for letting users know when their connection to a FileMaker host is fully secured or not. That connection can be secured by using the SSL encryption option that is available on FileMaker Server and will provide you with Encryption-in-Transit of all data flowing between FileMaker Server and its clients (FileMaker Pro and Go and WebDirect). There is also a FileMaker feature that provides Encryption-at-Rest that protects the content of the files as they sit on FileMaker Server or in its backup locations but that is not part of this story.
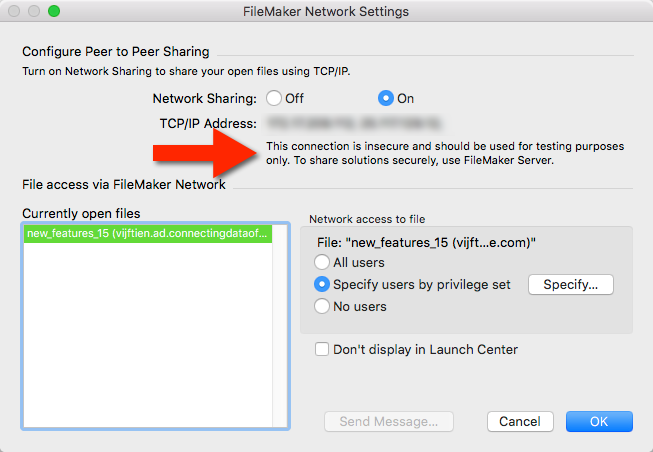
SSL encryption of that data flow is not available when you use a copy of regular copy of FileMaker Pro to host your files and share it with a number of users. To emphasize that, there is now a new warning that makes that perfectly clear as shown in Figure 1.
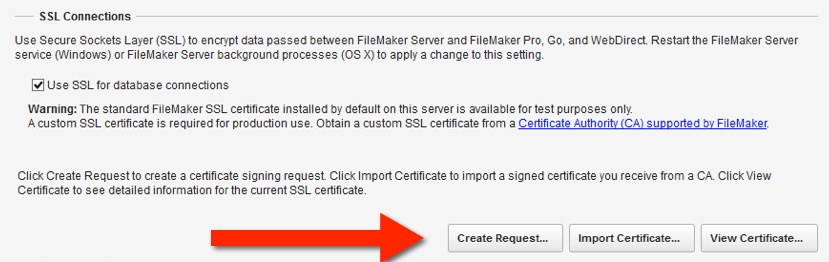
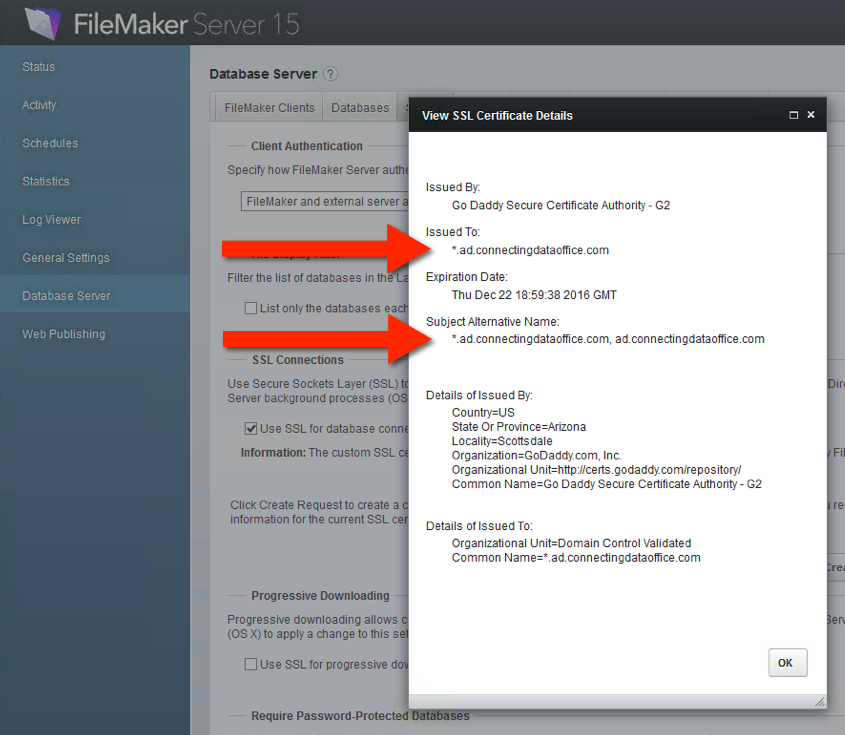
For a while now, FileMaker Inc. has been pushing all deployments towards using their own custom SSL certificate when that Encryption-in-Transit is required. And that message becomes louder in FileMaker 15. If you toggle on SSL but use the default provided FileMaker SSL certificate then the admin console clearly spells out that this should be for testing purposes only, not for a production deployment as shown in Figure 2 and 3.
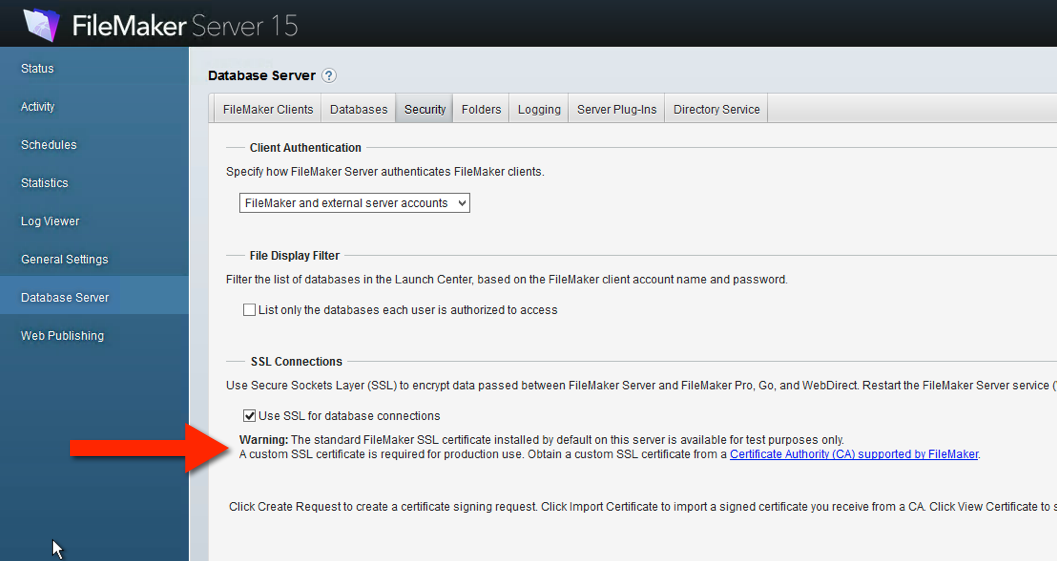
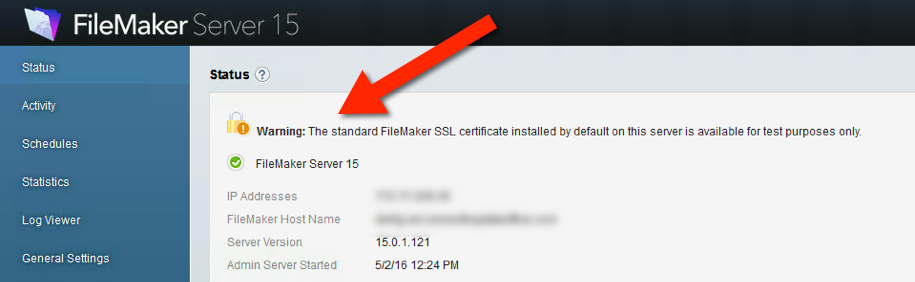
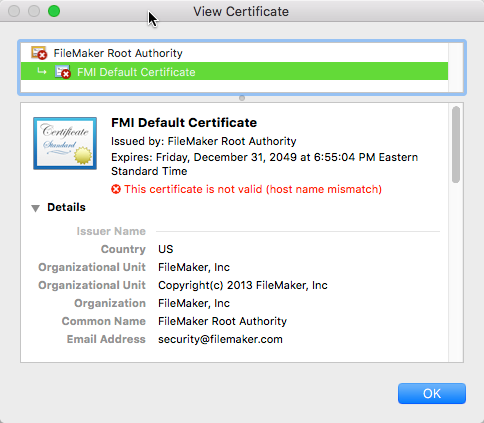
The whole point of using an SSL certificate of course is that it supposed to certify that the server you want to connect to is in fact the server that you are connecting to. That is done matching the name on the certificate to the name that you use to connect. The default SSL certificate is not issued in the name of your FileMaker Server so when you opt to use the default SSL certificate the client, the warnings will be shown to the clients.
When you use Open Remote or the Launch Center to connect to a FileMaker Server enabled with the default SSL certificate. You will be told immediately that the certificate could not be verified and the user can choose to connect or not connect.
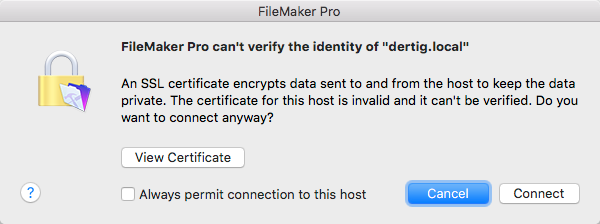
When you look at the certificate it will tell you there was a host name mismatch, which is to be expected.
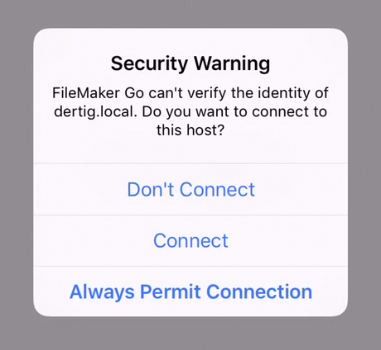
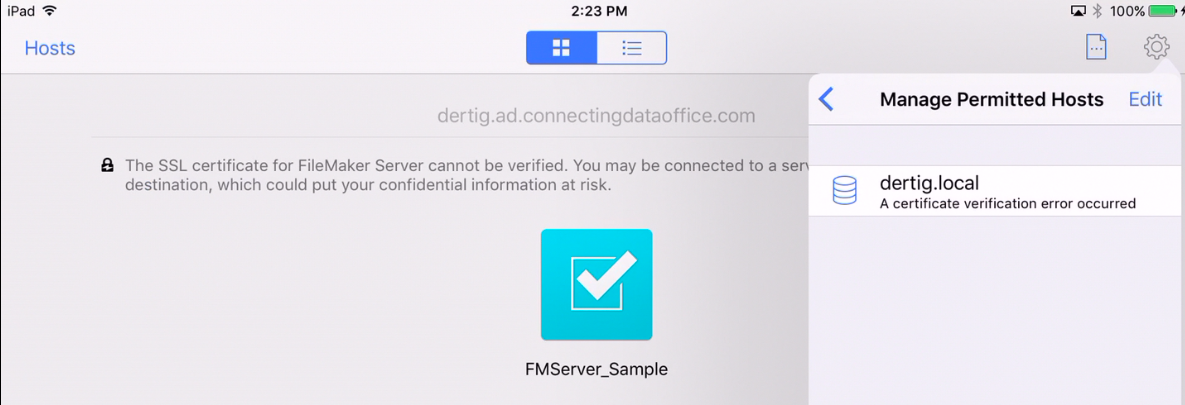
FileMaker Go 15 will display a similar message when you first connect to a FileMaker Server that uses the default certificate and then will continue the reminders when it shows the available files as shown in Figure 6 and 7:
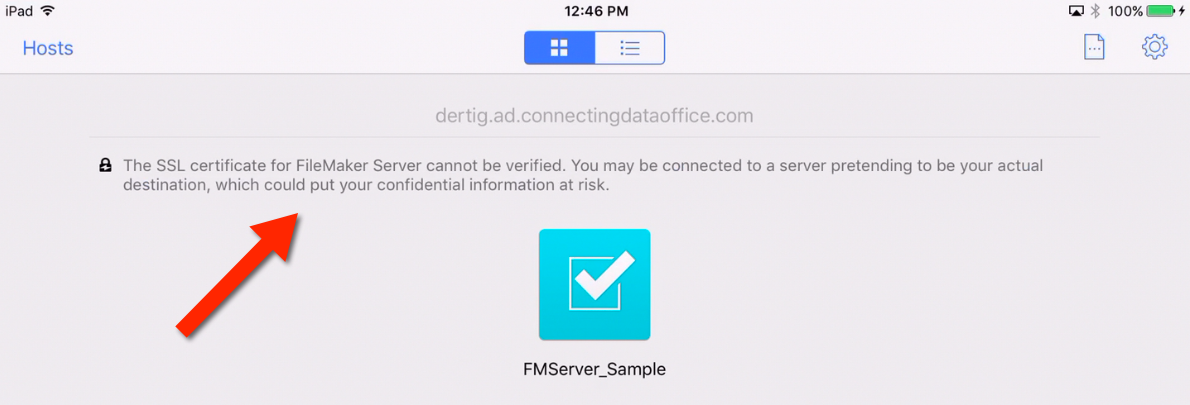
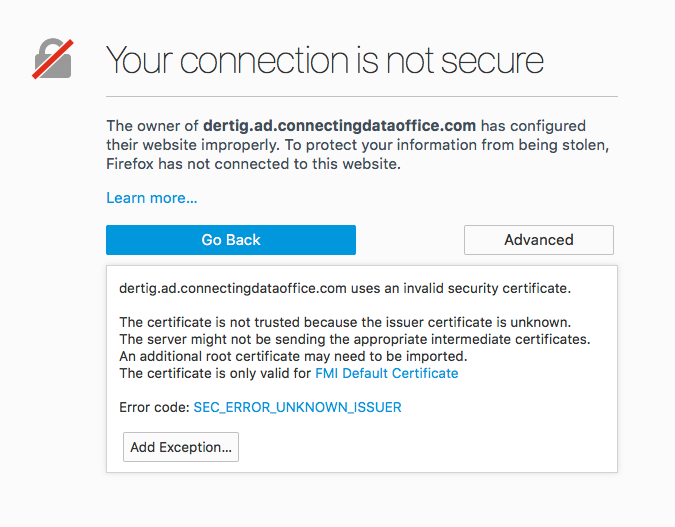
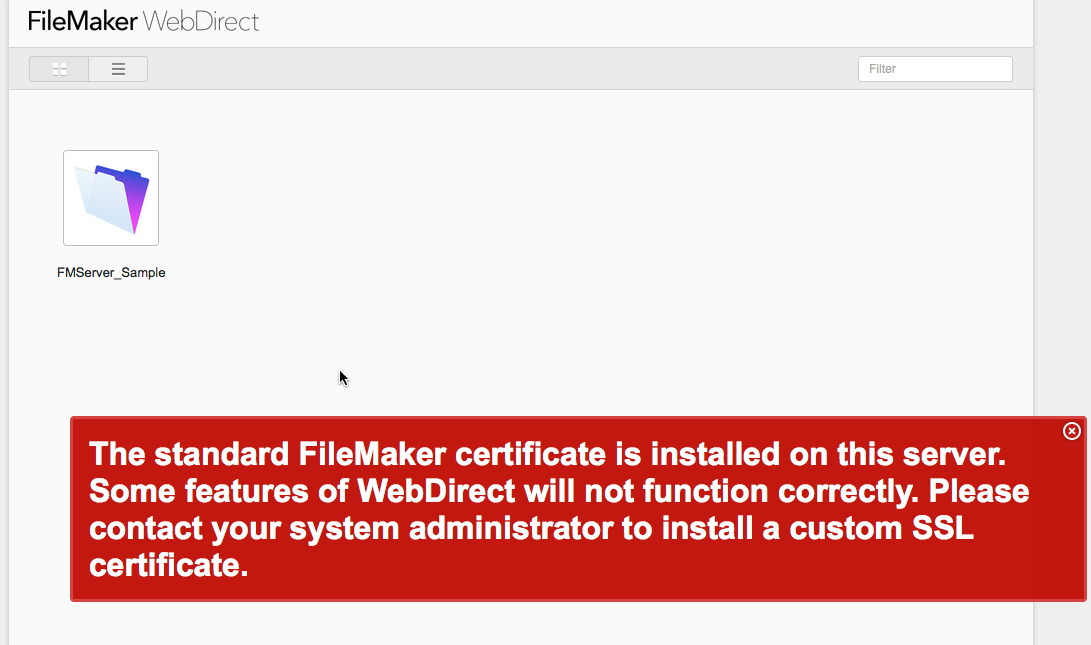
The same in WebDirect — the browser will typically be the first to pick up on the SSL certificate name mismatch as shown in Figure 8.
Even if you add an exception in your browser, WebDirect itself will make it clear that the deployment uses the default SSL certificate as shown in Figure 9.
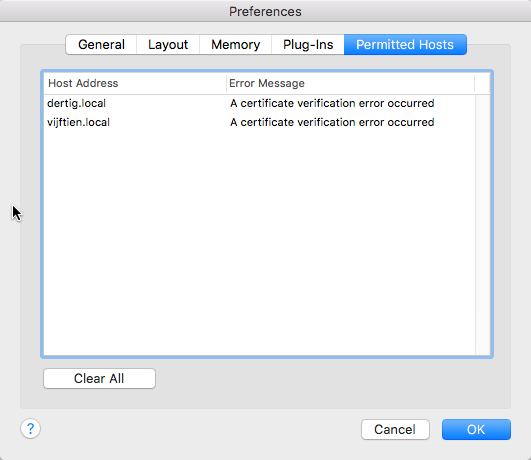
Looking back at the screenshots of the Filemaker Pro and Go clients, if you are wondering what happens when you check that, “Always permit connection”, the client itself keeps a list of the hosts that you’ve chosen to trust. See Figures 10 and 11. That is not something we as developers or IT admins can control, it is a client-by-client setting.
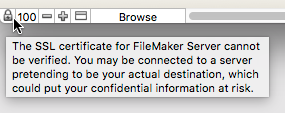
The long and short of it is: when SSL encryption is an important feature to your deployment then you want to make sure you use a custom SSL certificate. But… when you do use a custom SSL certificate make sure that the clients connect to the server using the name on the certificate. If you use launcher files or the FMP url protocol and link to the hosted file by the server’s IP address then the SSL connection will still fail because an IP address does not match the name on the SSL certificate and you will get this on the client as shown in Figure 12.
One of the pain points in setting up your FileMaker Server with a custom SSL certificate was that is … well a big pain. FileMaker Server 15 makes that a lot easier since it gives us the ability to generate the Certificate Signing Request (CSR) and importing the SSL certificate as shown in Figure 13.
And, oh by the way…
- we now have full support for wild card certificates and Subject AltName (SAN) certificates
- and a wider array of SSL providers
So all in all it is now a lot easier to secure your traffic with SSL, so no need to see all those nasty warnings 🙂
Security Enhancements
On the topic of security, here are some other very noteworthy security enhancements to the FileMaker platform:
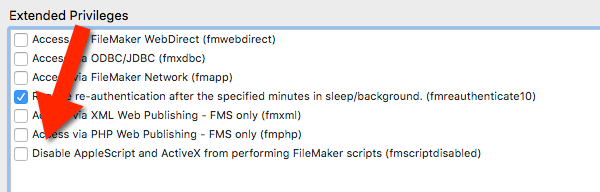
- The ability to disallow access to your solution from the ActiveX and AppleEvents external APIs. That setting is off by default so you need to explicitly turn it on if you want to take advantage of it.
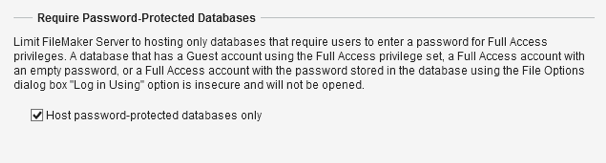
- A new setting on FileMaker Server that will prevent it from hosting files that have an account without a password. That setting is on by default.
Watch our videos for more FileMaker tips and techniques: